
How NIS2 will also help improve your cyber security

Scarecrow, more obligations, fines for non-compliance, the same halo as with GDPR. These are also the views expressed about the NIS2 directive. But why do they appear? What will the directive bring? Who will be covered by it, and from when? The questions are many, but one thing is clear. There is no need to panic, but it is a good idea to look at the state of cyber security in your organisation as soon as possible.
Jan Mareš
The essence of cyber security
Cybersecurity is a hot topic and will continue to be. Just as we know the principles of occupational health and safety (OHS) and fire protection (FP), our knowledge should be expanded to cyber security principles.
Cybersecurity today is no longer just about firewalls and antivirus, but also about setting up processes, rules and responding to current threats. It’s not just about IT, but also about the behaviour of employees and suppliers. Thus, we all have a responsibility for data security, not only in our professional duties, but also in our private lives.
What is NIS2
The NIS2 Directive (more specifically the Directive of the European Parliament and of the Council on measures to ensure a high common level of cybersecurity) is there to lay the foundations of cybersecurity for a wider range of organisations than was the case with NIS1, and thereby enhance the cybersecurity of EU Member States. This is to be achieved in particular by:
- by strengthening cooperation between the EU and the national supervisory authority, which in our case is the National Authority for Cyber and Information Security (NACIS),
- giving more powers to the supervisory authority (in the form of issuing warnings, measures or auditing organisations),
- adopting a national cyber security strategy,
- increasing fines for non-compliance,
- expanding regulated services – i.e. increasing the number of organisations that will be subject to the obligations (estimated at 6-12 thousand entities),
- introducing security measures for regulated services.
The requirements of the NIS2 Directive are nothing new in the field of cyber security. If your organisation was covered by the Cybersecurity Law or you have an information security management system in place, the news will probably be minimal for you. However, if cybersecurity is new to your organization, then yes, you will need to make a greater effort to comply with the new obligations. But there’s no need to panic.
How much time do we have
It is important to note that the NIS2 Directive itself does not directly impose any obligations on organisations. Although it came into force on 16 January 2023, it also states that Member States have 21 months to incorporate the requirements of the Directive into their local legislation. This is therefore a different situation from, for example, the DORA regulation, which we wrote about here.
An amendment to the Cybersecurity Law is expected to be issued within that timeframe, which is likely to allow some time for compliance. On the timeline, it would look like this:
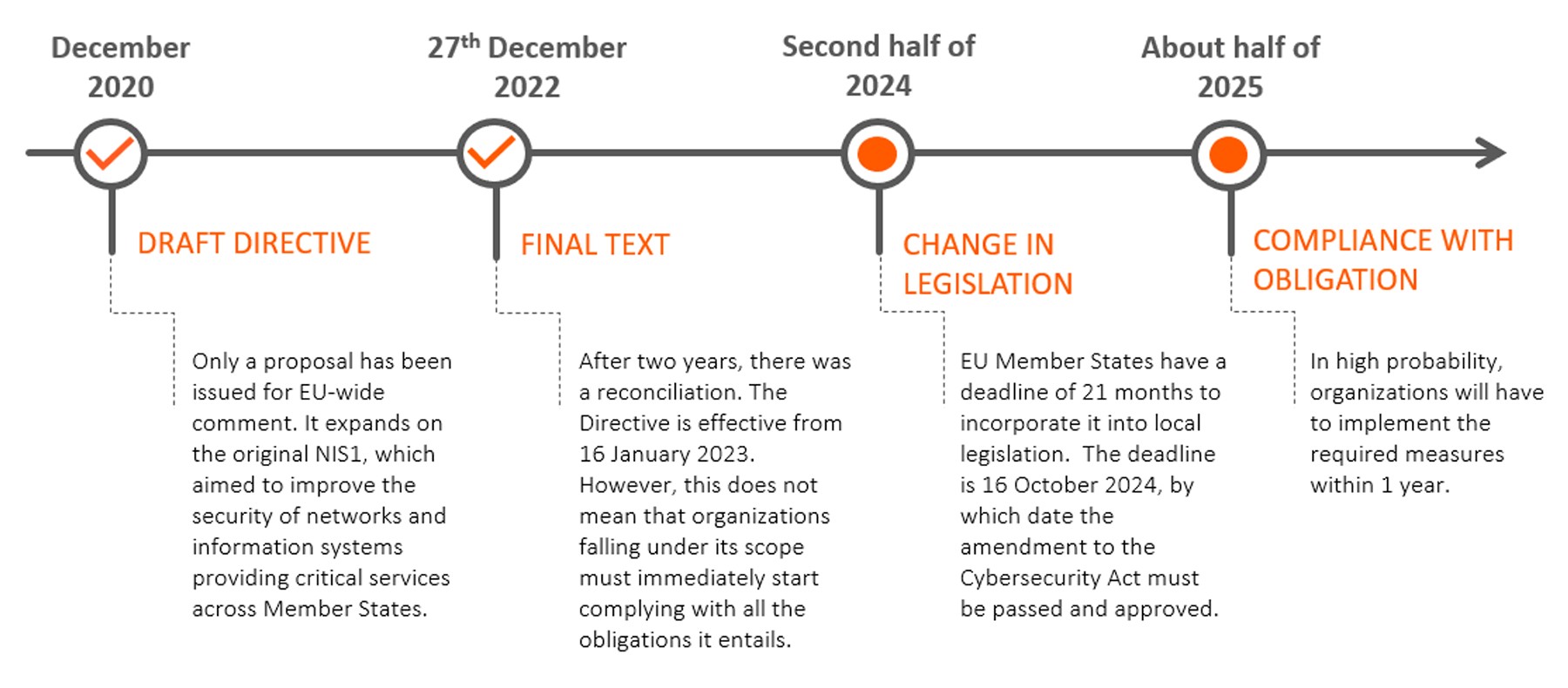
From this depiction, one could conclude that there is plenty of time and cybersecurity is not something that needs to be addressed. The opposite is true. Cybersecurity should not be underestimated, even in the light of what is happening in the world. Responsible organisations are addressing it continuously and not waiting for new legislation.
What the new draft Cybersecurity Law says
In the second half of January this year, the National Cyber Security Institute (NCSI) has already elaborated the requirements of the NIS2 directive and issued a draft of the new Cyber Security Act and its decrees. Thus, we know that some obligations will be even stricter than required by the NIS2 Directive. In general terms, organisations will have to:
- identify whether they are covered by the Act (unless determined by the NCIS itself),
- register with the NCIS Portal,
- determine the scope of cybersecurity management,
- report cyber security incidents,
- inform customers of incidents and threats,
- implement countermeasures to reduce risks,
- manage the supply chain,
- implement organisational and technical security measures.
How do you find out what specifically your organisation will need to comply with?
The first thing to do is to look at the draft Regulated Services Decree to see if it lists the service you provide. If so, you have met the first criterion for identification.
The second criterion is the size of your organisation. If you are a large or medium-sized enterprise, you will be subject to the obligations. However, beware – some small businesses providing a listed service may also fall under the new law.
Also, if you are a micro or small enterprise and your parent organisation is abroad, the number of employees is added up. So, you need to look at this carefully and identify if your organisation’s service is listed in the decree.
You can use this overview page produced by the NCIS on NIS2 to do this.
Like the NIS2 directive, the draft new law divides regulated services into two groups. The Directive provides a division into Essential and Important, which did not sound clear in the Czech language. Therefore, the draft new law and its decrees foresee a division into higher and lower obligation regimes. It implies obligations for organisations to implement the following organisational and security measures:
HIGHER REGIME OF OBLIGATIONS
ORGANISATIONAL MEASURES:
- Duties of senior management
- Security roles
- Management of security policy and documentation
- Asset management and risk management
- Supplier management
- Human resources security
- Change management
- Acquisition, development and maintenance
- Access Control
- Cyber event and incident management
- Business Continuity Management
- Cybersecurity auditing
TECHNICAL MEASURES:
- Physical security
- Communications network security
- Identity management and authentication
- Access Authorisation Management
- Detection of cyber security events
- Logging of security and relevant operational events
- Evaluating cyber security events
- Application security
- Cryptographic algorithms
- Ensuring availability of regulated service
- Securing industrial, control and similar specific technical assets
LOWER REGIME OF OBLIGATIONS
ORGANISATIONAL MEASURES:
- Ensuring a minimum level of cyber security
- Responsibilities of senior management
- Security roles
- Management of security policy and documentation
- Asset management
- Supplier management
- Human resources security
- Change management
- Acquisition, development and maintenance
- Access Control
- Cyber event and incident management
- Business Continuity Management
TECHNICAL MEASURES:
- Physical security
- Communications network security
- Identity management and authentication
- Access Authorisation Management
- Detection of cyber security events
- Application Security
- Cryptographic algorithms
- Ensuring availability of regulated services
- Security of industrial, control and similar specific technical assets
There are several differences between the two modes. They differ in some measures and in the way they are implemented. An example is the security roles (persons with different responsibilities to deal with cybersecurity), where the higher regime describes four roles and the lower regime only two.
There is also a difference in the potential fines for non-compliance: for the higher regime, the fine is set at up to €10 million or 2% of worldwide annual turnover. For the lower regime, the fine is set at up to €7 million or 1.4% of worldwide annual turnover. These are therefore not low amounts.
How to deal with this information?
I understand the views and concerns expressed in the introduction to this article. They are usually based on the expectation of additional work and additional expenditure, the return on which will not be quick (perhaps more likely none).
However, it is important to remember that any security measures that will be mandatory (and which are also based on international information security management standards and best practices over a number of years) have one goal: to protect your organization’s data and business, and by extension, your customers.
Cyber incidents are on the rise, and no organisation can guarantee that the next one won’t be perpetrated against it – no matter how interesting we think we are to cyber criminals. So, solve cyber security now, regardless of legislation – either on your own or with expert help. Above all, keep your data safe, whether on local servers or in the cloud.


